Cyber Crime Identify & Action
Cyber Crime Identify & Action
Cyber crime is on the rise, and the costs of experiencing a cyber attack are now higher than ever. After all, modern companies are hugely reliant on their IT systems and continued access to data, meaning cyber attacks can cause business downtime. Additionally, there can also be PR damage if customer data is compromised. At Fifosys, we use various techniques to help our clients build their defences against cyber security threats.
Security Audit
We can work with you to carry out a complete internal security audit, examining your current IT infrastructure, technologies, systems and processes, and identifying any issues needing addressing. From there, we will work with you to create an action plan that will allow you to address these problems, in line with your strategic goals. The purpose of a security audit is to establish is a future proof plan and roadmap, so that you understand where you are now, where you want to be, and how we can help you get there.
Penetration Testing
During a Penetration Test, we mimic the activities of malicious hackers and, in turn, can help you to identify your weaknesses. We test the strength of existing IT security systems, challenge the effectiveness of IT security policies and verify compliance with industry security standards to reveal the real strengths and weaknesses of your IT security infrastructure. Our penetration test service comes with clear reports full of practical recommendations to help you address previously unknown vulnerabilities.
The service includes the following:
A thorough approach comprising of external penetration testing against all sites and provided subnets
Practical suggestions for improvements to existing security products and services, such as patching known vendor or service vulnerabilities and activating additional security controls
Recommendations for extra IT security products and services, if appropriate, with business justifications
Insight into possible attack methods and behaviours, which are used in security monitoring systems to help detect intrusions quicker.
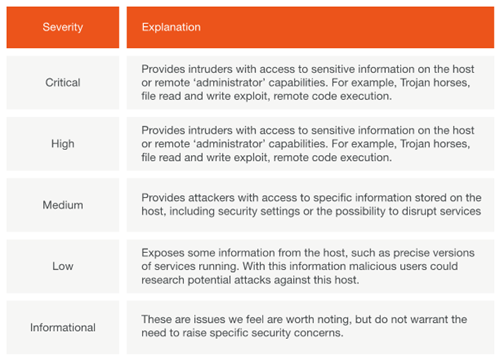
What will a Penetration Test identify?
To conduct the test, we use various tools to check for vulnerabilities, exploit any found vulnerabilities, scan ports and test access. The report will classify issues discovered in one of the following five severities:
Social Engineering Awareness Training - SEAT
What is SEAT?
Social Engineering Awareness Training, or SEAT, helps you and your business cope with evolving cyber threats. You can invest in the best cybersecurity systems around, but if you or your employees give the wrong information to the wrong people, it will still fail you. SEAT aims to provide your business with the knowledge needed to tackle social engineering attacks, including phishing, spear-phishing and impersonation.
How is SEAT Implemented?
Fifosys have a comprehensive SEAT program, designed to reduce the threats associated with social engineering attacks. We evaluate the knowledge level of the current staff by testing them against several social engineering campaigns. We then run through the results and work with you to prioritise training activities. The training can take the form of short bite-size training videos, online assessments, face-to-face training or a combination of all three. Additionally, we will also provide continuous engagement, maximising uptake and ensuring staff are up to date with new threats.
Get in touch to learn more.